Showing posts with label Xtreme. Show all posts
Cyber Law × Internet × Websites × Xtreme
 Meet Kristina Svechinskaya, the hot Russian hacker (allegedly). She has
been dubbed the 'world's hottest female hacker' and allegedly hacked her way
into American bank accounts. This sexy Russian 22-year-old is alleged to be
part of the Eastern European ZBot cyber-criminal gang. She and nine others
recently appeared in court in New York accused of using hacking software to
skim millions from American bank accounts.
Meet Kristina Svechinskaya, the hot Russian hacker (allegedly). She has
been dubbed the 'world's hottest female hacker' and allegedly hacked her way
into American bank accounts. This sexy Russian 22-year-old is alleged to be
part of the Eastern European ZBot cyber-criminal gang. She and nine others
recently appeared in court in New York accused of using hacking software to
skim millions from American bank accounts.
NEWS says
Called the ‘world’s sexiest computer hacker’, Kristina Svechinskaya was arrested in New York earlier this month, accused of being a part of an internet fraud ring alleged to have used malware and trojan viruses to steal $35 million from US bank accounts.
‘World’s sexiest computer hacker’ Kristina Svechinskaya to appear in court in connection with multi-million dollar internet fraud scam
 With big blue eyes, long dark hair and a sultry expression,
its hard to believe there is an internet debate on whether or not Kristina
Svechinskaya is hot enough to be the next Anna Chapman. I'm sure you remember
Anna Chapman, the sexy Russian spy that who over-shadowed her male
co-conspirators when they were all arrested for espionage. Obviously because
she was sexy, female and captured the imagination of the American public
fixated on James Bond-esque Russian spy stereotypes of sultry, sexy, seductivefemale spies who James Bond always conquers in the end. They fit the bill.
With big blue eyes, long dark hair and a sultry expression,
its hard to believe there is an internet debate on whether or not Kristina
Svechinskaya is hot enough to be the next Anna Chapman. I'm sure you remember
Anna Chapman, the sexy Russian spy that who over-shadowed her male
co-conspirators when they were all arrested for espionage. Obviously because
she was sexy, female and captured the imagination of the American public
fixated on James Bond-esque Russian spy stereotypes of sultry, sexy, seductivefemale spies who James Bond always conquers in the end. They fit the bill.
There even Anna Fermanova, who turned out not to be a Russian spy, but had a momentary notoriety as one just because she fit the bill after Anna Chapman went back to Russia.
Now there is Kristina Svechinskaya. She may not be a 'spy' exactly, but she is an alleged sexy Russian hacker who is said to have appeared in a New York City court to face the charges against her in tears, as well as in skin-tight jeans and sexy calf-high boots. Maybe its all about image.

.jpg)
Svechinskaya may or may not be a hacker. It is more likely she is a 'mule' who helped to transport information rather than gather it.
Kristina Svechinskaya has been charged with one count of conspiracy to commit bank fraud and one count of false use of passports. That's not how I would define hacking. Prosecutors claims that Svechinskaya was recruited to join a 'mule' organization that had numbered over two dozen participants and had contact with computer hackers and individuals who could provide fake passports.

Furthermore, she is alleged to have opened at least five bank accounts under her own name and under the aliases 'Anastasia Opokina' and 'Svetlana Makarova' into which $35,000 stolen from victims was fraudulently deposited.
.jpg) There's nothing really there to suggest, even if she was
proven guilty, that she's a hacker though
There's nothing really there to suggest, even if she was
proven guilty, that she's a hacker though Oh, pheshaw! People would rather think she was THE hacker anda spy to boot. That's just sexier.
Oh, pheshaw! People would rather think she was THE hacker anda spy to boot. That's just sexier.
Kristina Svechinskaya, was charged along with 37 people for their part in an Eastern European-based bank-hacking scheme. The group is alleged to have used hacking software, the Zeus Trojan computer virus, to steal $3 million from American small businesses and individuals bank accounts.
So why would the internet have to debate whether Kristina Svechinskaya is sexy enough? Apparently, its her name that might be the problem. Its a mouthful.
Read about her and see her photos click here.
Suggested by Bhargav Reddy
Xtreme
Today
we are going to see How to install backtrack 5 on Smartphones and
tablets which run on android.For this we have certain Required. Ofcourse
the main will be the Android smartphone with 2.1+. Though I recommend
4.0+.In my case ill be using Micromax a110 smartphone.
Requirements:
1.Back | track 5 Arm architecture which can be downloaded from the official website of the Back | track Here.
2.A smartphone/tablet which needs to be rooted since it requires root permission to run certain scripts. (micromax a110 as example)
3.Following Android Apps:
BUSYBOX : It acts like a installer and uninstaller.it needs root permission to run.it has gpu cores and can run linux kernals on android . Link
Superuser: This app just grants a superuser power to your phone just like “su” does for linux. Link
Terminal Emulator is app that runs a terminal console in android .Link
AndroidVNC is a tool for viewing VNC in Android. Link
2.A smartphone/tablet which needs to be rooted since it requires root permission to run certain scripts. (micromax a110 as example)
3.Following Android Apps:
BUSYBOX : It acts like a installer and uninstaller.it needs root permission to run.it has gpu cores and can run linux kernals on android . Link
Superuser: This app just grants a superuser power to your phone just like “su” does for linux. Link
Terminal Emulator is app that runs a terminal console in android .Link
AndroidVNC is a tool for viewing VNC in Android. Link
Installation:
1.Extract the backtrack folder “BT5-GNOME-ARM” to folder named “BT5” on the root of sd.That’s the top level of the SD card.
2.Open up the Terminal Emulator
3.Type the command “cd sdcard/BT5”
4.Run this command and you will see root@localhost.
su
sh bootbt
Operating Systems × Windows × Xtreme

If you are college/school students, you may curious to hack the admin password in your college or school system. This post is going to help you to crack the any type of windows accounts passwords. Learn how to hack the windows admin password.
Note : Please use Google search to download the latest version of the software.
To Crack Windows password we will be using Ophcrack ( 90 % success rate) and free version oF KON-BOOT (100% success rate ).
Download Ophcrack
The first thing we will need to do is download the CD image from
Ophcrack’s website. There are two options to download, XP or Vista, so
make sure you grab the right one. The Vista download works with Windows Vista or Windows 7, and the only difference between XP and Vista is the “tables” Ophcrack uses to determine the password.

Once the .iso file is downloaded, burn it to a CD using Imgburn, Nero.....( Google search to download the latest version of the software)

If
you are going to be cracking your password on something that doesn’t
have a CD drive, such as a netbook, download the universal USB creator
from PenDrive Linux (http://www.pendrivelinux.com/universal-usb-installer-easy-as-1-2-3/).
A USB drive will not only run faster but you can also use a single USB
drive for Windows XP, Vista, and 7 if you copy the needed tables to the
drive.
 |
To create a USB drive that works with all versions of Windows, download the free password tables from Ophcrack’s website.

Now extract the tables to \tables\vista_free on the USB drive and they will be used automatically by Ophcrack.
Boot from CD/USB
Boot the computer from the CD or USB drive that you created.

Note: On some computers you may have to go into the BIOS settings to change the boot order or push a key to show the boot menu.
Once the disk is done booting, Ophcrack should start automatically and
will begin cracking the passwords for all of the users on your computer.

Note: If the computer boots and you only have a blank screen or
Ophcrack doesn’t start, try restarting the computer and selecting manual
or low RAM options on the live CD boot menu.

If you have a complex password it will take a lot longer than simple passwords, and with the free
tables your password may never be cracked. Once the crack is done you
will see the password in plain text, write it down and reboot the
machine to login. If your password isn’t cracked, you can also log in as
one of the other users with admin rights and then change your password
from within Windows.
With the free tables available you will not be able to crack every 90% password.
KON-BOOT :
Getting
onto someone’s computer when they are not around can be a tall task.
Most people have passwords on their machines, thwarting any would-be
pranksters.
Well, this problem can be solved with a small tool called KON-BOOT.
Rather than cracking a Windows password, KON-BOOT bypasses it and lets
you into the computer without typing one in. Then, when you restart,
everything is back to normal, that is, everything you didn’t change for
the computer prank.
To get KON-BOOT, go to their website http://www.piotrbania.com/all/kon-boot/index2.html
Scroll down to the following for the download that will boot Windows.
You will have to unzip the downloaded file and then burn the CD image or
on pendrive. After that is done, you are ready to start the pranking
fun.
Wait until a friend leaves his computer and make sure you have enough
time to get the deed done. Pop in the CD and turn on the computer,
making sure you boot from the CD. This may require you to hit F12 at
the BIOS screen and choose to boot from the CD. You’ll know you’re
there when you see the following.
At any time, hit Enter and you should see an ASCII art logo draw onto
the screen and a few loading dialogs that should look something like
this.
The computer should then boot Windows and, if everything worked, you
shouldn’t be prompted for a password. Now you’re ready to do your
computer prank.
After you’ve finished your dirty deeds, you can just take out your disk
and reboot the computer. It will boot as normal, with your playful
changes waiting to be discovered.
KON-BOOT is a powerful tool and should be used with discretion.
Clearly, it could be used for malicious purposes, but no one like a
malicious person.
Credits Pirated Thief
Credits Pirated Thief
Xtreme
BAD week for the hacker community

The Internet lost a few great minds this week. [Aaron Swartz], confronted with an upcoming federal trial for his actions in downloading and releasing public domain academic articles from JSTOR, hanged himself this week. As one of the co-developers for RSS, the Creative Commons license, and slew of other works, [Aaron]‘s legacy expanded the freedoms and possibilities of the most important human invention since the book.
Perhaps overshadowed in the news by [Aaron] is [Fabio Varesano], the man behind FreeIMU and Femtoduino. He died of a sudden heart attack at the much too young age of 28. The RC helicopter/plane/drone and HCI/physical computing communities lose a great mind with [Fabio]‘s passing.
There is talk on the Dangerous Prototypes forum of continuing the development of FreeIMU, a project it seems [Fabio] worked on alone. We’d love to see someone pick up the reigns of the FreeIMU project, hopefully after doing a run of the current hardware and donating the proceeds to [Fabio]‘s family. reported by Hack a Day.
Andriod × Mobiles × Softwares × Xtreme
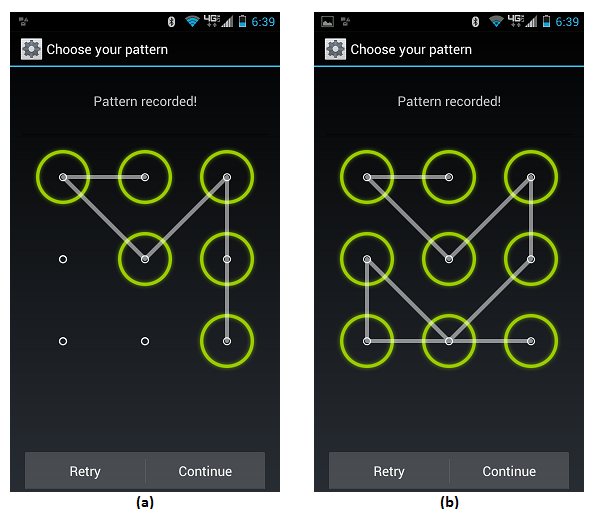
CRACK Pattern Lock
Hello friends.....,
I am here with a new cool hack....,
i m here to show you how to hack android pattern
lock...,
lock...,
Yup!! the android pattern lock can be hacked!!!
Follow the procedure...
Thing you need:-
- USB cable for your mobile
- ADB tool (download from here)
{Note:- USB debugging must be on }
NOW LOCK YOUR MOBILE WITH YOUR DESIRED PATTERN.., AND CONNECT TO PC USING USB CABLE AND FOLLOW THE PROCEDURE GIVEN BELOW......
Android Debug Bridge (adb) is a versatile command line tool that lets you communicate with an
emulator instance or connected Android-powered device. It is a client-server program that includes
three components:
Procedure:-
- A client, which runs on your development machine. You can invoke a client from a shell by issuing an adb command. Other Android tools such as the ADT plugin and DDMS also create adb clients.
- A server, which runs as a background process on your development machine. The server manages communication between the client and the adb daemon running on an emulator or device.
- A daemon, which runs as a background process on each emulator or device instance.
- Download ADB tool from the given link
- Extract it. (password is - raipurtricks.in)
- Now open cmd.exe from the given tool,
type adb.exe [enter] - Now type the following command-
adb shell [enter]
rm /data/system/gesture.key [enter]
reboot [enter]NOW WAIT.. YOUR DEVICE WILL REBOOT.. AND WILL
ASK FOR PATTERN...,
MAKE ANY PATTERN.., AND YOUR DEVICE WILL BEUNLOCKED !!!!
Facebook × Xtreme

In the field of computer security, phishing is the criminally fraudulent process of attempting to acquire sensitive information such as usernames, passwords and credit card details by masquerading as a trustworthy entity in an electronic communication. Communications purporting to be from popular social web sites, auction sites, online payment processors or IT Administrators are commonly used to lure the unsuspecting. Phishing is typically carried out by e-mail or instant messaging, and it often directs users to enter details at a fake website whose look and feel are almost identical to the legitimate one. Even when using server authentication, it may require tremendous skill to detect that the website is fake.
Read more for the Phishing Tutorial
Now i am going to explain you “How to do phishing?”
Just Follow the steps as indicated below and if you face any problems you are free to post your problems in comments section.
Step 1: The First Step in Making the site is to register an account at 000webhost (if you have account than you can skip first 2 steps)
Step 2: Now Go to your email account that you gave and confirm your account with confirmation link
Step 3: Now Download this FILE
Step 4: Now Go to 000webhost and Log into your account.
Step 5: Now when you are logged into your account click on the Go to Cpanel in front of your domain that you had registered, and then Go to File Manager under Files and log into it.
Step 6: Now Click on the Public_html.
Step 7: Now click on the Upload button, choose the files that you have downloaded, to be uploaded.
Step 8: Now any one who visits your site would be taken to the Fake Facebook Login Page.
After they enter their Username and Password, they will be taken to
another page that will show them error. So there is less chance that it
will be detected.
NOTE::: To access the input data ( Usernames and Password ) go to
public_html, there u will find a text file open that to view the
usernames and password.
**FOR EDUCATIONAL PURPOSES ONLY!**
eBook × Facebook × Internet × Linux Mobile × Mobiles × Operating Systems × Websites × Xtreme
Take this article as a Precautionary measures.
With this technique you can hack ID's of your best friends...
Requirements:
- A cellphone that can receive texts
- A Slave :P (Must be in your friend list)
- Patience
Step 1 : Pick a Target and start a conversation with him/her.
Conversation :
You: Hey can u help me really fast?!?
slave: Sure what do u need?
You: I told a friend of mine that i don't have a phone and hes asking whose phone number this is: (Your number here), I told him its urs but he does not believe me…
So can you umm put this as your phone number for like 5 mins??
slave: Ok how?
You: Just go to account settings and on the left it says mobile click on that and put this number in: ( Your number here) and company is: ( Reliance, Airtel etc whatever phone company you use)
slave: K its asking for a confirmation code…
You: (You should get a confirmation code) Ok heres the code: (your code here)
slave: Kk done
You: brb in 5 mins!
Step 2 : Logout or use a different browser and open Facebook , then click on Forgot Password.

Now enter his/her details and click on Search. Then you will get a option of recovering ur Facebook ID with ur email id or Mobile. Click on Mobile. Then click send code, your phone should receive a code , enter that code. Thats it you are DONE!!!
To make sure they dont get their account back i suggest changing the email and deleting any other email registered on the account.
Its works !!!


.jpg)
.jpg)
























